The destination router is the gateway of last resort. A technician is configuring a router to allow for all forms of management access.

Marcie Lewis On Twitter Learning Process Teacher Planning Teaching
VLANs require routing between them.
. The banner motd command is used to display a message when a user attempts to log into the router. It provides a way to make announcements to those who log in to a router. Change all the bits to the right of the line to 0s to determine the network number 01000000 or 64.
VLANs separate hosts into logical networks. It prevents real time processing and increases latency sensitivity. Question 1 5 points Which of the following characteristics describes an edge router.
The traffic from a source IPv4 address of 1920288 is being translated by router RT2 to reach a destination IPv4 address of 192168254253. This in turn helps defend against network attacks like spoofing. The line would be drawn between the 0100 and the 1101 because the subnet mask is 28.
Enable inbound vty Telnet sessions. Add multiple connections between the switches and the edge router. Edge routers are a crucial part of the edge firewall protecting the enterprise network by securing and characterizing incoming IP traffic.
It seats at the edge of the backbone of the network and can connect to the core routers. Set the domain name. A stub router or an edge router connected to an ISP has only one other router as a connection.
Which of the following characteristics describes the application layer. VLANs allow any host plugged into the switch to become a member of the virtual segment. As part of each different type of access the technician is trying to type.
The top or seventh layer of the OSI model which is responsible for enabling communications with host software including the operating system. Draw a line showing where the subnet mask 1s end. The traffic from a source IPv4 address of 192168254253 is being translated to 1920288 by means of static NAT.
The function of routing traffic from an external source received on a specific pre-defined IP address and port combination also known as a socket to an internal resource server. It increases the amount of data that it sends over the network and in this way it allows for data exposure in transit. All the following characteristics describe VLANs except.
A default static route works in those situations because all traffic will be sent to one destination. It passes on the heavy lifting on enormous and heavy data sets to the on-premise network. An entrance or exit point to a controlled space B B.
VLANs can be used to apply security policies and filtering to different segments. It can be wired or wireless and will distribute internet data packets between one or more networks. This characteristic makes them superior than hubs and bridges because they simply view the network on a link-by-link basis The packet handled by router may include destination address packet priority level least-cost route minimum route delay minimum route distance and route congestion level.
Edge router connection to the ISP Explanation. A form of VPN establishing a secure VPN over trusted VPN connections C. Which of the following characteristics describes an edge router.
Configure the IP domain name on the router. But it will not distribute internet data packets within networks. Which of the following describes dynamic packet filtering.
Which two statements describe the characteristics of fiber-optic cabling. Generate the SSH keys. It is designed to operate in the internet backbone or core.
A form of cryptography in which each encryption key is used once before being discarded D. Which statement correctly describes the NAT translation that is occurring on router RT2. A router does the followingAccepts a frame from a medium De-encapsulates the frame Determines the best path to forward the packet.
The last device owned and controlled by an organization before an ISP or telco connection B. Edge routers enable remote employees to connect to the corporate LAN through the network edge. Which term describes the cumulative value of an asset based on both tangible and intangible values.
There are four steps to configure SSH support on a Cisco router. For example with Device 1 the final octet 77 is 01001101. View Test Prep - CH 3 Quiz from FIN 2243 at The University of Oklahoma.
A The last device.

Internet Routing Protocol Article Khan Academy

Different Types Of Routers In Networking Fs Community

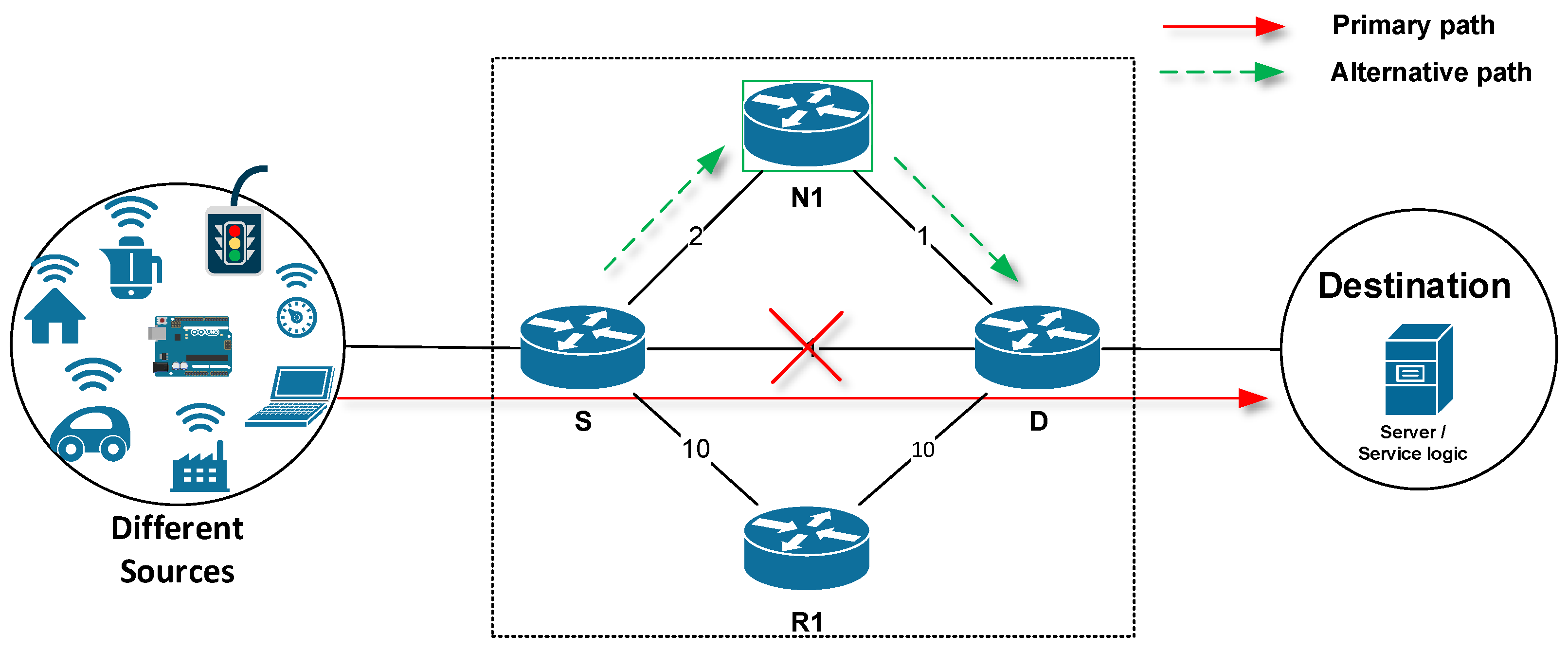
Applied Sciences Free Full Text Enhanced Bit Repair Ip Fast Reroute Mechanism For Rapid Network Recovery Html


0 Comments